UMC UTRECHT WINS DUTCH PRIVACY AWARDS 2026 WITH ROSEMAN LABS TECHNOLOGY | Learn more
Get insights in seconds, from data you can't see
Roseman Labs makes it fast and easy for organizations to work together on sensitive data to generate Trusted Collective Intelligence - without giving up control, and in full regulatory compliance.
Winner Dutch Privacy Awards 2026
The Privacy First Foundation awards UMC Utrecht, using Roseman Labs technology, the 2026 Dutch Privacy Award. The prize recognizes outstanding initiatives that advance privacy protection in the Netherlands.

Sandbox with Irish pillar banks
One of only seven companies selected to participate in the Central Bank of Ireland’s Innovation Sandbox Programme, Roseman Labs has been working alongside two Irish pillar banks to demonstrate how encrypted computing can enable institutions to collaborate on anti-fraud and anti-money laundering efforts.

€5M Series A
Roseman Labs Gains Backing from Global Leaders to Scale Trusted Collective Intelligence

15 questions for the Founders
Read more about our Founders' experience as entrepreneurs and what it takes to grow a company to Series A.

Work with encrypted data seamlessly
Reducing crime, preventing fraud and protecting lives requires intelligence that spans beyond any single organization or data source.
Roseman Labs enables encryption-in-use analytics on private data from multiple participants, so organizations can make decisions based on real data, without sharing raw records or compromising data security.
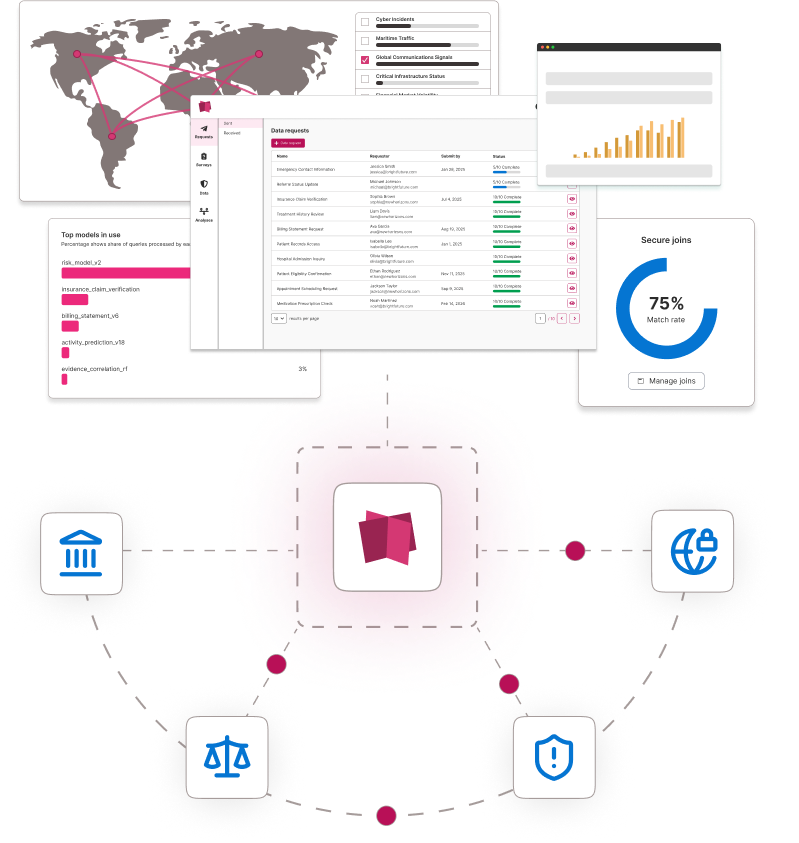
Advanced technology
Trusted Collective Intelligence
Get fast, reliable, and format-flexible insights with encryption-in-use data analytics. Our encrypted computing platform retains data richness and delivers results in seconds.
Scalable platform
Ready today
50+ functions, open standards, and seamless integration. Deploy instantly, no heavy lift required. From a few partners, to hundreds—computing on millions of records.
Trusted
For real world networks
Stay in control of who can see and access what. Fully GDPR, NIS2 & AMLR compliant. Backed by global privacy recognition and security certification.

Join us at an event!
Connect your data.
Supercharge your tech stack.
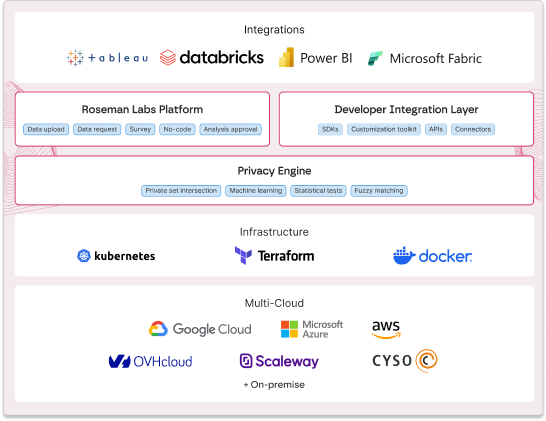
Platform
Secure insights
without tradeoffs
- Fast and reliable results without exposure
- High performance with elastic scale and speed
- Ready for analysts, no cryptography expertise needed
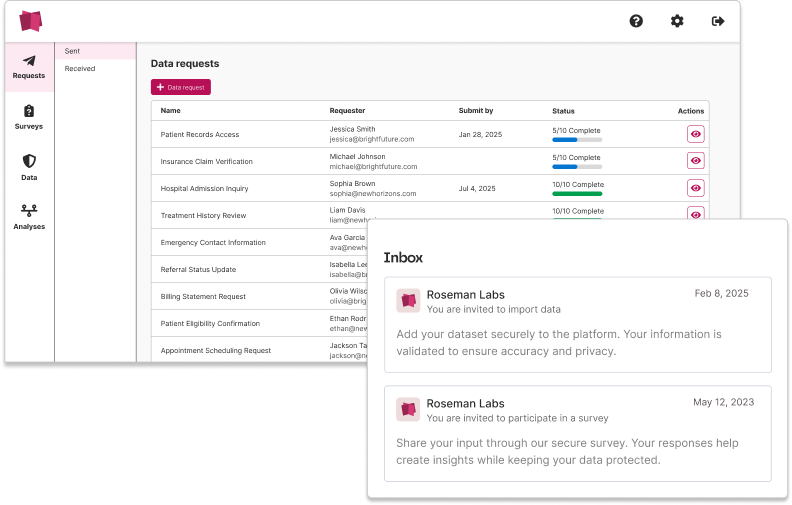
You stay in control
Full data sovereignty
across every layer
- Fits into your existing stack
- Deploy on any cloud or on-premise
- Connect to your tools via APIs or no-code workflows
50 +
Functionalities
150 +
Organizations using the platform
100,000 +
Records per second
A European answer
to a global problem.
National Security
Detect and prevent threats through cross-agency intelligence fusion, without exposing classified or sensitive data.
Anti-Financial Crime
Enhance AFC efforts through signal-sharing and suspicious pattern detection, in a confidential and compliant manner. Drive down costs by stopping fraud, avoiding penalties and reducing burden on auditors.
Healthcare
Study patient journeys, improve care coordination and determine treatment effectiveness by connecting data sets from different healthcare providers or other partners.
Customer story
NCSC accelerates collaboration against cyber attacks
The National Cyber Security Centre combines the data of public and private partners to discover the nature and scale of cyber attacks.
What our customers say
“With Roseman Labs we solve a long-standing privacy problem that until now has really limited our ability to improve care for children in vulnerable situations.”

UMC Utrecht
“It's fast, it's safe, it's accurate. We get the insights we need to help our citizens, without ever seeing their personal data."

Gemeente Rotterdam
“Working with data in healthcare is often made so complicated and time consuming. Roseman Labs makes it fast and easy to conduct targeted healthcare research.”

NVvP
"We support specific initiatives vital for our European and national cyber security and strategic autonomy. Roseman Labs' solution is such an initiative."
Explore your use case
Speak with the team
Navigating how to work with sensitive data can be complex, but we're here to help. Talk with one of our Directors to learn how you can easily generate new insights on private data by integrating Roseman Labs.
Whether you already know your data collaboration partners, or are exploring a use case, don't wait to get started - get in touch!

Customer story
The City of Rotterdam tackles developmental delay in infants with encrypted computing
See the video to learn how.
Trusted
Our commitment to security
- Stay in control of your data with approval flows
- No single point of failure with encrypted data distributed across three separate trusted servers
- Enterprise-grade security with SSO, 2FA and more

Encrypted data spaces
Get to know the world’s fastest and most user-friendly encrypted computing platform.


